Go as far as possible in the fewest steps
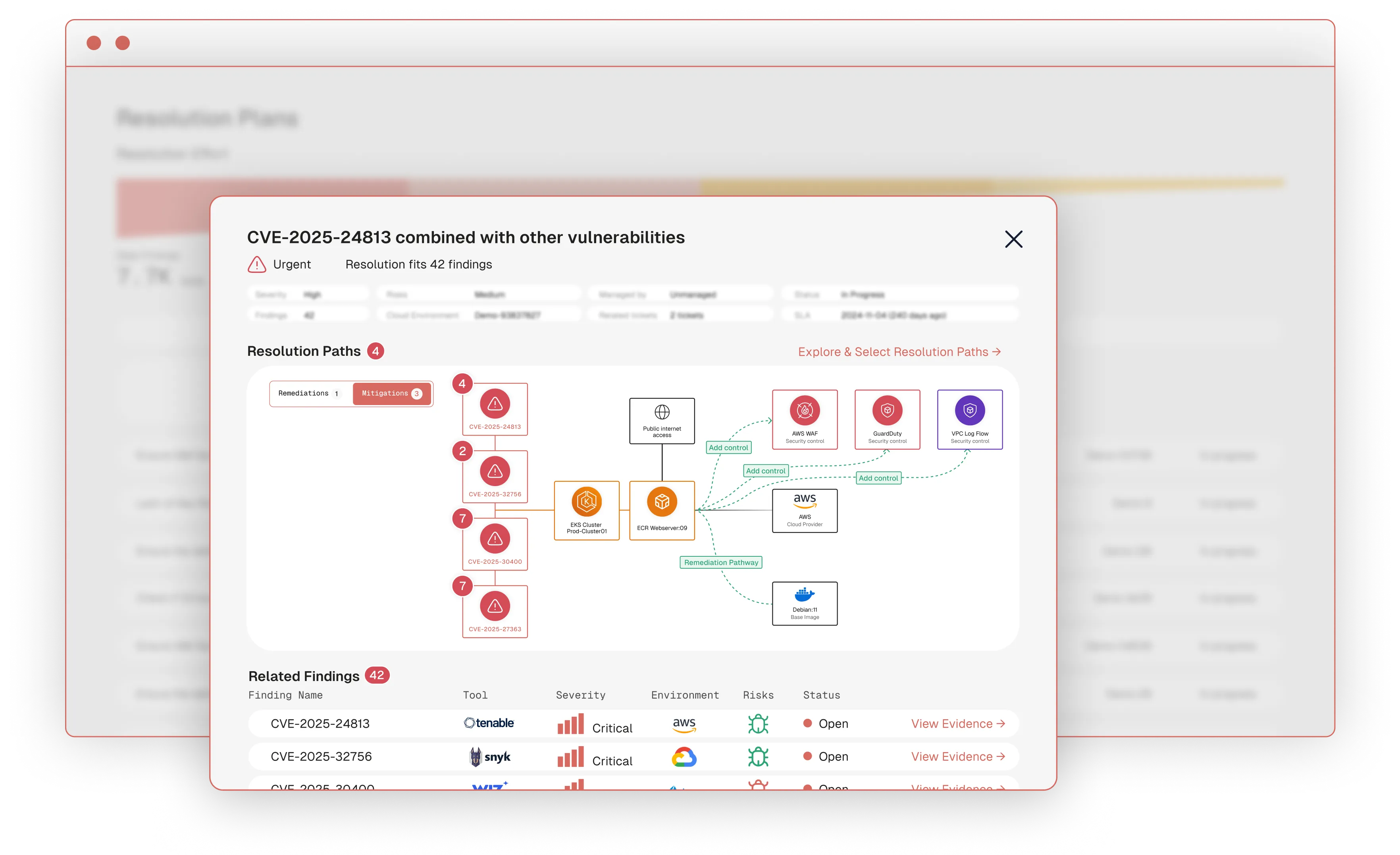
The ZEST platform analyzes infinite options for resolution simulating the impact and effectiveness of available fixes, remediations, and mitigations across groups of risks. ZEST finds the path of least resistance so you can eliminate the most risk with the least effort.
Speed
Eliminate weeks of back and forth between security, DevOps, and engineering teams to validate findings, review code, understand root causes, and research the best fix.
Precision
ZEST’s AI agents tackle complex remediation tasks from root cause analysis and prioritization all the way to fully guided remediation and mitigation.

The path was always there.
Now you see it.
The ZEST platform is powered by a multi-agent AI system - a network of AI agents working in concert together to illuminate the most direct pathways for eliminating exposure.
Creates a graph and structure database that represents your technical DNA, including all assets and services, DevOps deployments, existing tooling, controls, and policies.
Pinpoints the origin of the problem, tracing it back to the associated asset, problematic lines of code, IaC tool, and DevOps owner.
Prioritizes findings based on risk, exploitability, reachability, business criticality, remediation effort and impact.
Simulates the implementation of patches, package updates, IaC and code fixes to determine which resolution paths resolve the most vulnerabilities at once.
Analyzes problematic code and generates replacement code based on the organization’s infrastructure and policies.
Correlates security tool findings with globally defined cloud security policies, ensuring that risks already mitigated by existing policies are excluded.
Analyzes cloud security services and guardrails and detects available mitigation measures to deprioritize unexploitable risks.
Leverages the outcomes of numerous agents to determine the best path for resolution, tailored to the organization's unique technical DNA and environment.

ZEST is a SaaS platform hosted in Amazon Web Services (AWS). Each customer gets their own tenant hosted in either the US or Europe.
Deployment takes just minutes. Simply create a read-only cloud account for ZEST. From there, simply connect your security tools using our built-in connectors, and start seeing your risks mapped to resolution pathways.
ZEST natively integrates with CSPM, vulnerability management, SCA, and ASPM solutions. We currently support 50+ integrations. Check out our integrations page.
Nope. CSPMs focus on identifying risks and attack paths that are feeding your backlog. ZEST resolves them. Think of us as the “action” layer that turns findings into fixes.
Absolutely. ZEST is built for multi-cloud environments and supports AWS, Azure, and GCP - giving you a unified view of exposure and centralized approach to remediation.
No. ZEST only has read-only access. We don’t change anything in your cloud environment directly. ZEST integrates seamlessly with workflow systems like ticketing and messaging platforms to guide patching and other remediation efforts. We provide all the context and data needed so your teams can take quick, informed action while remaining in complete control.
ZEST’s AI remediations are driven by real-time context from your cloud and DevOps systems. Our agents simulate every fix on a digital twin of your environment, recursively validating the outcome before suggesting changes, ensuring accuracy, safety, and reliability. We are a natural part of your existing deployment & QA processes.
No. ZEST does not send any customer data to external AI services. We use an internal, in-house LLM that runs within our secure infrastructure in AWS. All customer data is kept strictly within ZEST’s environment in accordance with the highest data security standards and is never shared with third-party AI platforms.
ZEST is SOC 2 compliant, demonstrating our commitment to maintaining a high standard of data security and privacy.
Yes. ZEST helps with multiple CTEM phases by helping you prioritize what matters most, validating different resolution pathways, and mapping exposures to the most efficient remediation actions.




.webp)


.svg.png)